Introduction To Network
 Bedirhan Özsoylar
Bedirhan ÖzsoylarWhat is a Network?
A network is a system that allows computers and other digital devices
(printers, phones, etc.) to connect to each other for data sharing
and communication.
Simply put, it is a group of connections that enables devices to communicate with each other.
Main Purpose:
Shared use of resources such as files, programs, and hardware
Fast and reliable exchange of information between users
The Internet is the largest and most widespread example of a network in the world.

(Example image of network structure)
What is LAN?
LAN (Local Area Network) is a type of network in which computers and other devices
within a home, office, or school in a small and limited area are connected
to share data and communicate.
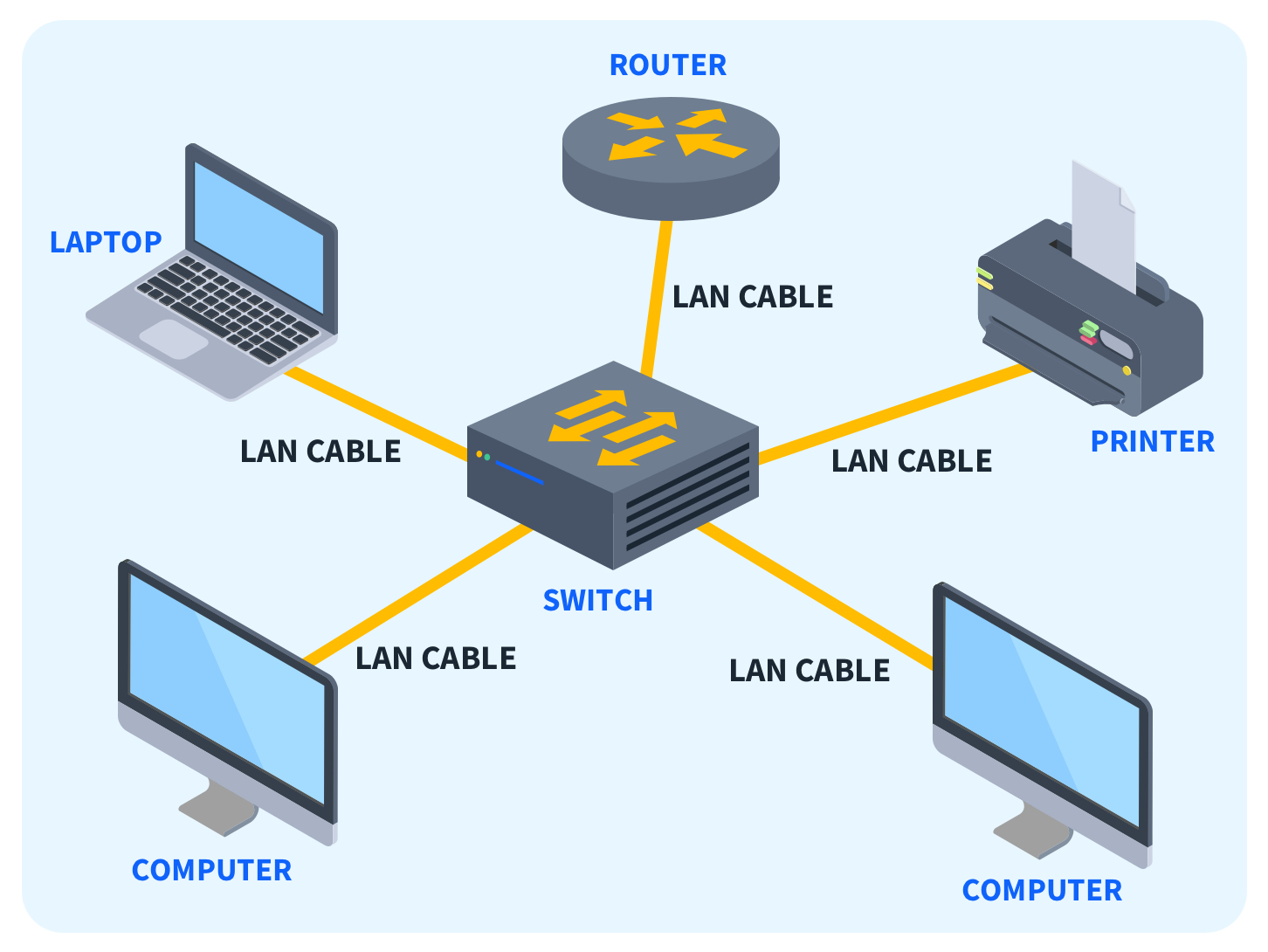
(Example image of a local area network)
What is WAN (Wide Area Network)?
WAN is a wide area network that connects devices located in different geographical regions.
It covers large distances, and the internet is the most common example.
Features:
Connects across cities, countries, or continents
High-speed data transmission is possible
Uses security and management protocols

(Example image of a wide area network)
Network Components
Below are the basic hardware and software components that make up networks, along with their English names.
Hardware Components
1. Network
- The structure that enables data communication between devices.
2. Router
- A device that directs data packets between networks.
3. Switch
- A device that enables data exchange between devices within the same network.
4. Access Point (AP)
- A device that allows wireless devices to connect to the network.
5. Modem
- Converts the signal received from the Internet Service Provider into digital data and establishes a network connection.
6. Network Interface Card (NIC)
- A hardware component that enables devices to connect to the network (Ethernet card or wireless card).
7. Hub
- A simple connection device that sends data to all devices in the network at the same time (rarely used today).
8. Server
- A device that provides services and data to clients.
9. Client
- A device that connects to the network and receives data or services from the server (PC, mobile device, etc.).
10. Cable
Provides physical connection between devices in the network.
- Types: Ethernet (UTP), fiber optic, coaxial...
11. Patch Panel
- A hardware component that combines network cables in an organized and accessible way.
12. Load Balancer
- A device that directs network traffic to multiple servers, improving performance and continuity.
13. Power Supply Unit (PSU)
- A power component that ensures uninterrupted operation of network hardware.
Software / Logical Components
14. IP Address
- The identity of each device on the network (IPv4 or IPv6).
15. DNS Server
- The system that translates domain names into IP addresses (e.g., google.com → 142.250.190.14).
16. DHCP Server
- A system that automatically assigns IP addresses and network settings to devices.
17. Firewall
- Ensures security by monitoring incoming and outgoing data on the network.
18. Proxy Server
- A server that acts as an intermediary between the user and the internet (provides anonymity, filtering, and caching).
19. Virtual Private Network (VPN)
- Provides secure and encrypted network connection through remote servers.
20. Cloud Service
- Services offered over the internet such as storage, computing power, or applications (example: Google Drive, AWS, Azure).
21. Network Operating System (NOS)
- A special operating system that manages network resources and enables sharing among users (example: Windows Server, Linux server distributions).
22. Intrusion Detection/Prevention System (IDS/IPS)
- Security software/systems that detect (IDS) and prevent (IPS) threats targeting the network.
Network components work together to enable data communication.

(Example image of network components)
What is a Router?
A router is a network device that connects different networks and directs data packets to the correct destination.
It operates at Layer 3 (Network Layer) of the OSI model.
Main Functions
Routes data packets based on IP addresses
Enables communication between different networks (e.g., home network and the internet)
Hides local network IP addresses using NAT (Network Address Translation)
May include firewall features for security
Use Cases
Home and office internet connections
Networks of ISPs (Internet Service Providers)
Connecting different subnets in large organizations

What is a Switch?
A switch is a network hardware device that connects devices within the same network and delivers data to the correct device.
It operates at Layer 2 (Data Link Layer) of the OSI model.
Key Features
Learns MAC addresses to optimize data transmission
Sends data only to the target device (unlike a hub, which sends to all ports)
Reduces collisions and unnecessary traffic
Improves LAN performance
Use Cases
Office and home networks
Distribution after the modem
Connecting IP cameras, printers, computers

What are Managed and Unmanaged Switches?
1. Unmanaged Switch
Simple, plug-and-play devices
No configuration required by the user
Preferred in small and simple networks, such as homes or small offices
Provides basic data transmission, lacks advanced features
2. Managed Switch
Can be configured and managed by the user
Has advanced features such as VLAN, traffic management, security, and monitoring
Used in large and complex networks, corporate environments
Used to optimize network performance and detect issues
Summary
| Feature | Unmanaged Switch | Managed Switch |
| Setup | Easy, no configuration | Complex, configurable |
| Control | None | Available |
| Features | Basic connectivity | VLAN, QoS, monitoring, security |
| Usage Area | Small networks | Large/corporate networks |
What is a Layer 3 Switch?
A Layer 3 Switch is a network device that combines the functions of both a Switch and a Router.
It operates at Layer 3 (Network Layer) of the OSI model.
Key Features
Connects devices within a LAN like a Layer 2 Switch
Performs IP routing between different networks like a Router
Operates at high speed thanks to hardware-based routing
Commonly used in large networks for managing traffic between VLANs
Layer 3 Switch vs Router
| Feature | Layer 3 Switch | Router |
| OSI Layer | Layer 3 (Network) | Layer 3 |
| Layer 2 Functionality | Yes (performs switching) | No |
| VLAN Support | Yes | Limited |
| Performance | High (hardware-based routing) | Lower (software-based routing) |
| Usage Area | Corporate LAN, data centers | WAN connections, internet access |
When Is It Used?
To route traffic between VLANs (Inter-VLAN Routing)
In environments where both switching and routing are needed
When high bandwidth and low latency are required
Example Scenario
In a company, three VLANs are set up for three separate departments:
VLAN 10 – Finance
VLAN 20 – IT
VLAN 30 – Marketing
A Layer 3 Switch is used to enable data exchange between these VLANs.
This allows fast and secure routing of data without needing an additional router.
What is a VLAN?
VLAN (Virtual Local Area Network) is a method of creating logically separated small network groups on the same physical network.
Key Features
There is no direct communication between different VLANs (ensures security)
Multiple VLANs can be created on the same physical switch
Isolates network traffic, improving performance
Simplifies management and increases security
Use Cases
Separating departments into different VLANs in a company
Isolating guest and internal networks
Segmenting network traffic
What is a Firewall?
A firewall is a security system that controls incoming and outgoing traffic in a network and blocks unauthorized access.
Key Features
Filters network traffic (based on IP, port, protocol)
Blocks harmful or unauthorized connections
Can be implemented as both hardware and software
One of the fundamental components of network security
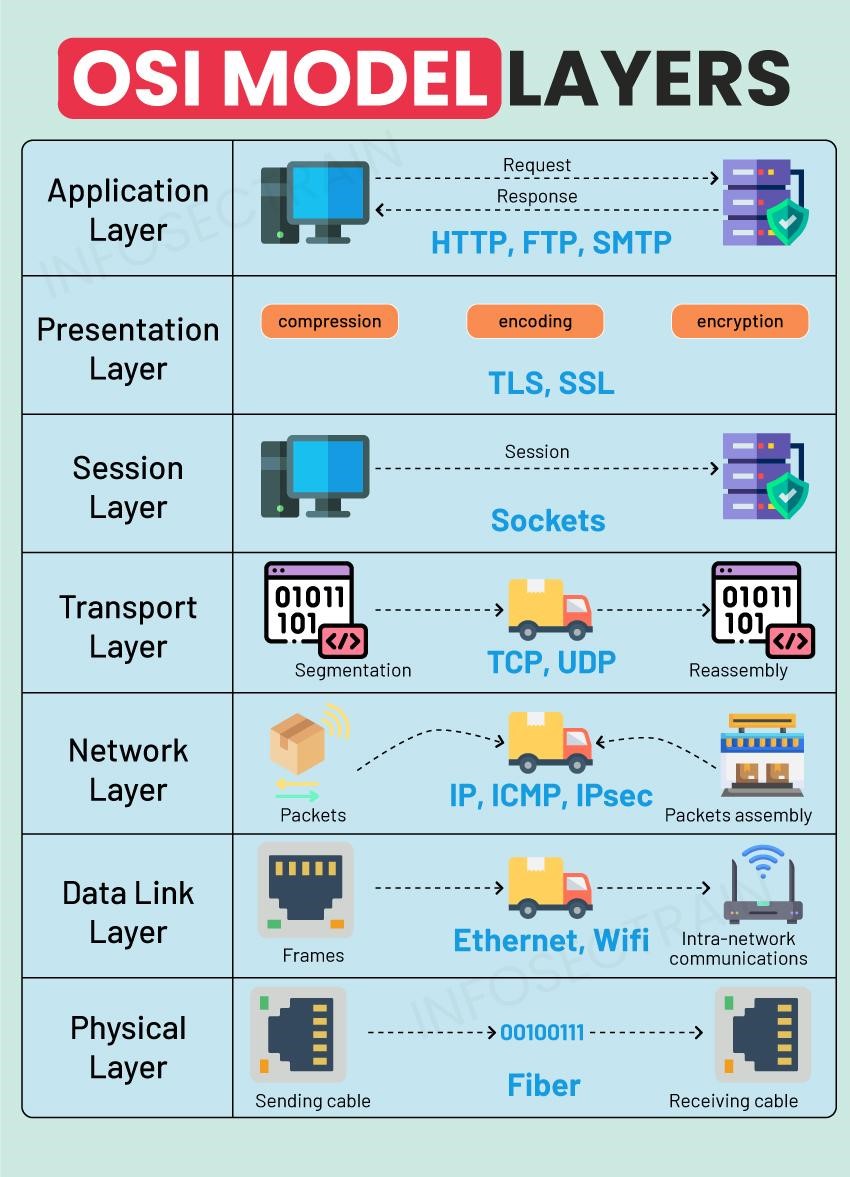
OSI Model
The OSI (Open Systems Interconnection) model divides network communication into 7 layers:
Physical Layer
- Transmission medium and physical connections (cables, electrical signals)
Data Link Layer
- Sends data packets as frames, performs error control (MAC addresses are used here)
Network Layer
- Routes data between different networks (IP addressing, routing)
Transport Layer
- Ensures reliable and ordered transmission of data (TCP, UDP protocols)
Session Layer
- Establishes, manages, and terminates connections between two devices
Presentation Layer
- Handles data formatting, encryption, and compression
Application Layer
- The closest layer to the user; supports applications such as file transfer, email, and the web
Network Protocols
Network protocols are rules and standards that enable devices to communicate with each other. Here are some commonly used network protocols:
1. TCP (Transmission Control Protocol)
Connection-based, provides reliable data transmission
Guarantees ordered and complete delivery of data
2. UDP (User Datagram Protocol)
Connectionless, fast but less reliable
Used in real-time applications like audio and video
3. IP (Internet Protocol)
Enables data to be packetized and routed to its destination
Has two versions: IPv4 and IPv6
4. HTTP (HyperText Transfer Protocol)
- Enables web pages to be transmitted between client and server
5. HTTPS (HTTP Secure)
- Secure version of HTTP, uses data encryption
6. FTP (File Transfer Protocol)
- Protocol used for transferring files
7. SMTP (Simple Mail Transfer Protocol)
- Used for sending emails
8. DNS (Domain Name System)
- Translates domain names into IP addresses
9. DHCP (Dynamic Host Configuration Protocol)
- Automatically assigns IP addresses and network settings to devices
10. ARP (Address Resolution Protocol)
- Converts IP addresses into MAC addresses
11. ICMP (Internet Control Message Protocol)
- Delivers error and status messages on the network (used by the ping command)

What is Broadcast?
Broadcast is a method of sending data to all devices on a network at the same time. In this type of communication, when the sending device sends a packet, all devices on the network receive this packet. In other words, data is spread to everyone without specifying a target address.
Broadcast is generally used in local networks (LAN). It is especially used in IP address assignments (for example, when a DHCP client says "I am here" to all devices on the network to get an IP) or in protocols like ARP.
Advantages:
No need to specify a target.
Effective in cases like discovery of new devices.
Disadvantages:
Creates unnecessary traffic.
May cause performance degradation in large networks.
What is Unicast?
Unicast is the transmission of data to only a single target device. It is the most commonly used transmission method.
Example: Sending data from a computer to a server.
What is Multicast?
Multicast is the transmission of data simultaneously to multiple but specific devices (a group). Instead of the entire network, only the devices registered in this group receive the data.
Example: Used in applications like live streaming, video conferencing.
Most Important Network Security Protocols
IPsec (Internet Protocol Security)
Encrypts network traffic, authenticates, ensures data integrity.
Especially used in VPN connections.
TLS/SSL (Transport Layer Security / Secure Sockets Layer)
Provides secure communication on the internet.
Used as HTTPS on websites.
Encrypts data and prevents third parties from reading.
HTTPS (Hypertext Transfer Protocol Secure)
Secure data transfer between web browser and server.
Uses TLS protocol.
SSH (Secure Shell)
Provides secure connection to remote servers.
Offers encrypted command line access.
Much more secure compared to Telnet.
WPA2 / WPA3 (Wi-Fi Protected Access)
Encrypts and protects wireless networks.
WPA2 is common for home and corporate networks.
WPA3 is newer and provides stronger security.
Routing Protocols
OSPF (Open Shortest Path First)
Link-state based interior routing protocol.
Creates the entire map of the network.
Selects the shortest path based on cost value.
Suitable for large and complex networks.
Provides fast recalculation and stable structure.
EIGRP (Enhanced Interior Gateway Routing Protocol)
Developed by Cisco (now open standard).
It is a hybrid: has both distance-vector and link-state features.
Makes smarter decisions based on network load.
Provides more flexible and faster routing.
BGP (Border Gateway Protocol)
Backbone of the internet, routes between different autonomous systems.
Is a path-vector protocol.
Makes decisions based on policies and rules.
Used by large-scale networks and Internet Service Providers (ISP).
Extra:
RIP (Routing Information Protocol)
A distance-vector based routing protocol.
Measures routes in the network by hop count.
Maximum hop count is 15; 16 or more means "unreachable".
Provides simple and easy setup, but not scalable for large and complex networks.
Routing information is sent regularly (usually every 30 seconds) to all neighbors.
Therefore, it responds slowly to network changes (has long convergence time).
Uses mechanisms like split horizon and hold-down timer to prevent loops.
In short: Suitable for small and simple networks, inefficient and outdated for large networks.
Service Discovery Protocols
DNS (Domain Name System)
Converts domain names to IP addresses.
It is the fundamental service discovery mechanism of the internet.
Allows people to easily access websites.
DHCP (Dynamic Host Configuration Protocol)
Assigns automatic IP addresses and other network information to devices on the network.
Devices use DHCP to identify themselves and connect to the network.
mDNS (Multicast DNS)
Allows devices to find each other in small local networks (LAN).
Sends DNS queries as multicast.
Used in systems like Apple’s Bonjour service.
SSDP (Simple Service Discovery Protocol)
Used for UPnP (Universal Plug and Play) devices to identify themselves on the network.
Common in home networks to discover devices like printers and media servers.
LDAP (Lightweight Directory Access Protocol)
Used for centralized directory services.
Stores and allows finding user, device, and service information.
Authentication Protocols
Kerberos
Central authentication service.
Performs secure authentication between users and services with a ticket system.
Commonly used in corporate networks and Microsoft Active Directory.
OAuth
Allows third-party applications to access without giving user account information.
Used as "Sign in with an app" option on services like Facebook and Google.
Authorization protocol; works together with authentication.
OpenID Connect
Protocol built on OAuth that provides authentication.
Used to securely share user information.
SAML (Security Assertion Markup Language)
XML-based standard.
Used for single sign-on (SSO) and sharing authentication information.
Often preferred in enterprise applications.
RADIUS (Remote Authentication Dial-In User Service)
Central authentication protocol.
Used for user authentication in VPNs, wireless networks, and network access devices.
NAT (Network Address Translation)
Technique that translates private IP addresses in the network to public IP addresses.
Private IPs of devices are hidden when accessing the internet, and communication is done via a single public IP.
Saves IP addresses and creates a security layer.
Commonly used in home and office routers.
Example: 192.168.1.10 (private IP) → 88.77.66.55 (public IP)
Subscribe to my newsletter
Read articles from Bedirhan Özsoylar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
