Microsoft 365 faces a widespread attack campaign aimed at stealing user accounts worldwide
 Lưu Tuấn Anh
Lưu Tuấn Anh
Overview
Recently, the cybersecurity team at Proofpoint discovered a large-scale phishing campaign targeting organizations and individuals using Microsoft 365. This campaign not only impersonates popular applications like SharePoint, Adobe, and DocuSign but also employs new, more sophisticated attack techniques that can help attackers bypass multi-factor authentication (MFA), which is considered one of the strongest defenses today.

Since early 2025, attackers have exploited phishing kits like Tycoon and ODx to easily conduct phishing campaigns. They use fake Microsoft OAuth applications to gain access to Microsoft 365 accounts and bypass MFA (Multi-Factor Authentication) using MITM (Attacker-in-the-Middle) techniques.

According to reports, nearly 3,000 accounts in 900 different Microsoft 365 tenants were compromised in 2025.
Attack Process
Initially, the attacker creates a fake OAuth application in the Microsoft Azure AD environment. These fake applications are named and designed with logos similar to reputable services like RingCentral, SharePoint, Adobe, DocuSign, or iLSMART. These applications only request minimal permissions (e.g., User.Read, offline_access) to avoid suspicion and easily deceive users.

Additionally, the attacker will set up a series of infrastructures to proceed with the next steps:
Command and Control (C2) server to store collected information.
Phishing kits (Tycoon, ODx) ready to handle the fake login step.
Intermediate CAPTCHA page to filter bots and avoid automated analysis.
Once everything is prepared, the attacker will send a phishing email from a previously compromised Microsoft 365 account. The email content often poses as a request for quotation (RFQ), a contract, or a notice requiring document confirmation. Inside this email is a link to Microsoft's OAuth authorization page.

And of course, this is a real Microsoft domain, which makes it very difficult for email filters to mark it as dangerous.

When users receive the phishing email and click on the embedded link, their browser immediately displays the legitimate Microsoft authorization page. This fake application will request two basic permissions:
View your basic profileMaintain access to data you have given it access to
If users allow these permissions, the fake app is granted an access token and refresh token, enabling data access without a password. Notably, even if users deny permission, the attacker continues the process—redirecting to a CAPTCHA and then to the phishing login page.
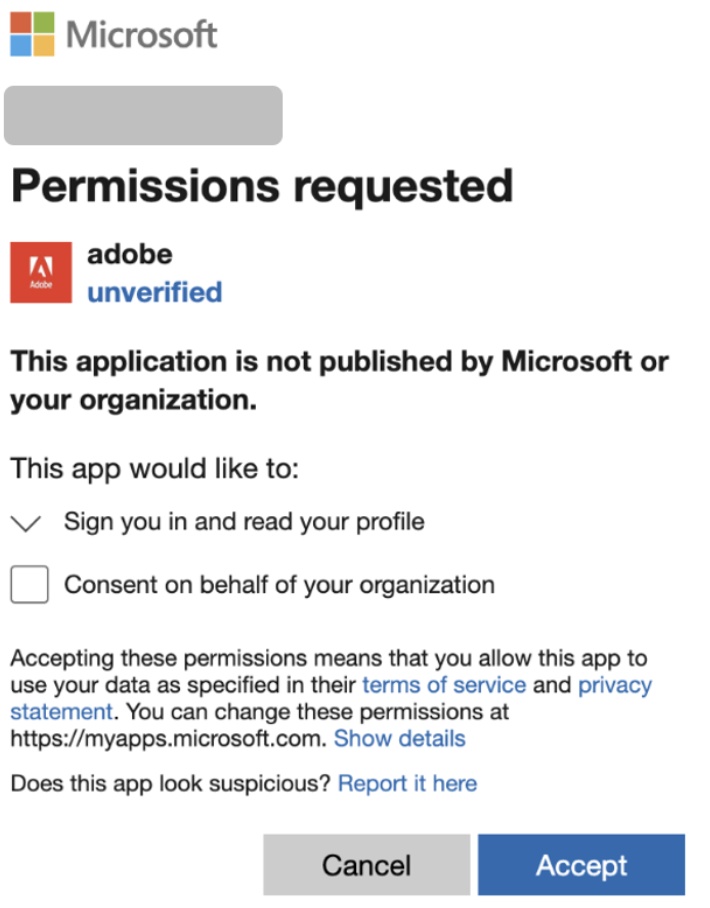
After being redirected and passing the CAPTCHA, the victim's browser is taken to a fake Microsoft login page containing the Attacker-in-the-Middle kit (Tycoon, ODx):
Proxies all communication between the victim and Microsoft.
Collects username, password, and MFA code in real-time.
Sends this data to the C2 server.
Finally, with the collected login information and MFA code, the attacker can easily:
Log into the victim's Microsoft 365 account.
Create email forwarding rules, read/extract documents, or send internal phishing emails to expand the attack.
Recommendations
- Protect User Accounts
Use FIDO2, Windows Hello, YubiKey, or Microsoft Authenticator push notification
Disable legacy authentication: Go to Azure AD > Conditional Access > Block legacy authentication
Regularly change passwords and clear sessions
Limit access based on roles (Least Privilege)
- Access Control and Intrusion Detection
- Enterprises should implement solutions to detect anomalies from internal accounts, such as excessive email sending, sending outside of work hours, or unusual repetitive behavior.
- User Awareness Training
Regular training on OAuth / AiTM phishing: Teach users to be suspicious of unfamiliar apps requesting permissions or unusual redirects to CAPTCHA or fake logins
Guide on checking URLs when logging in: Carefully verify the domain: only log in at
login.microsoftonline.comormicrosoft.com
Conclusion
The fake OAuth campaign using Tycoon/ODx clearly demonstrates the sophistication of modern phishing. With the ability to bypass MFA and exploit legitimate Microsoft authentication interfaces, this method makes it very difficult for users to detect. Organizations using Microsoft 365 need to update their security configurations, apply FIDO-based MFA, and maintain user awareness training to minimize risks.
IOC
Domain C2 & Tycoon
hxxps[:]//azureapplicationregistration[.]pages[.]dev/redirectapp
yrqwvevbjcfv[.]es
gmlygt[.]ru
hxxps://chikeukohandco[.]com/saas/Index.html
pw5[.]haykovx[.]es
Reference
Subscribe to my newsletter
Read articles from Lưu Tuấn Anh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
