More than 29,000 Exchange servers face a serious security vulnerability that leads to data loss and system takeover
 Lưu Tuấn Anh
Lưu Tuấn AnhOverview
On August 11–12, 2025, experts identified a critical vulnerability with the identifier: CVE-2025-53786 found in Microsoft Exchange hybrid – a system combining on-premises Exchange and Exchange Online on Microsoft 365. This vulnerability allows an attacker, if they have gained administrative control over the on-premises Exchange server, to escalate privileges to the cloud environment without leaving traces easily detected by standard Microsoft 365 logging tools.

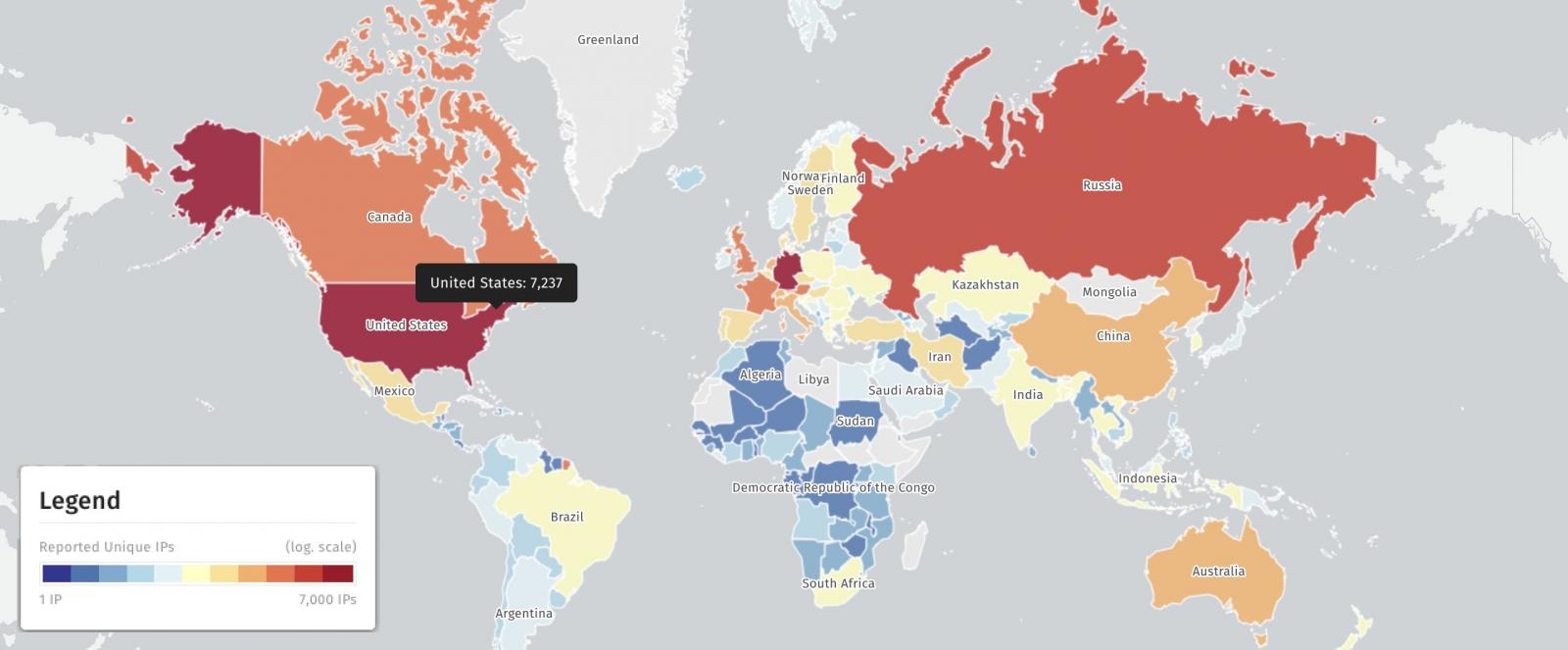
According to data from the security monitoring platform Shadowserver, as of August 10, 2025, there are 29,098 Exchange servers that have not yet been updated to fix this vulnerability. Of these, more than 7,200 are in the United States, over 6,700 in Germany, and more than 2,500 in Russia.
Vulnerability Description
Vulnerability Code: CVE-2025-53786
CVSS Score: 8.0 (High)
Description: Elevation of Privilege (EoP) vulnerability – allows an attacker to escalate privileges from the on-premises environment to the cloud environment (Exchange Online)
Attack Mechanism: Exchange Server and Exchange Online share a service principal in the hybrid configuration, creating a trust gap that can be exploited
Vulnerability Details

Initially, to exploit the vulnerability, the attacker needs administrative rights on the Exchange server (on-premises). Here, they will access the certificate file or export it directly from the on-premises Exchange server (usually stored in the
Program Files\Microsoft\Exchange Server\V15\OAuthdirectory or in the certificate store).After obtaining the “Private Key”, the attacker will create a fake OAuth Token by using the key to sign a JSON Web Token (JWT) in the form of a self-signed client assertion. This JWT will be sent to the Azure AD OAuth 2.0 token endpoint.
Example:
https://login.microsoftonline.com/{tenantID}/oauth2/token).
Next, with the fake token and by adjusting the "act-as" claims in the token, the attacker can impersonate any hybrid user account in the cloud (including admin).
Finally, after successfully impersonating a user, the attacker will perform a series of malicious actions they desire:
Read/write emails from Exchange Online.
Access files from SharePoint/OneDrive.
Execute remote PowerShell commands on Exchange Online.
Download data, deploy a backdoor in the cloud, or escalate to other SaaS systems integrated with Azure AD.
Recommendations
- Apply the latest patches and hotfixes
Update immediately to:
Exchange 2019: Cumulative Update 14 (CU14) or CU15
Exchange 2016: CU23
Install the April 2025 hotfix or a newer update that addresses CVE-2025-53786.
Ensure servers are not using EOL (end-of-life) versions.
- Revoke and renew OAuth keys
If you suspect or know that the on-prem system has been compromised, revoke the old OAuth certificate immediately.
Create a new private key and update the hybrid configuration.
Remove any unused keys to reduce the attack surface.
- Restrict permissions and separate environments
Limit on-prem admin rights only to accounts that truly need them.
Separate on-prem admin accounts from cloud admin accounts (do not share them).
Enable Privileged Access Workstation (PAW) for administrative accounts.
Conclusion
This campaign shows us how dangerous CVE-2025-53786 is, as it allows privilege escalation from Exchange on-premises to Exchange Online without easy detection. More than 29,000 unpatched servers are spread across many countries, and Vietnam is not exempt if organizations or individuals do not update and protect themselves.
Any organization using Exchange hybrid should quickly implement patches to avoid becoming an easy target for cybercriminal groups worldwide.
References
Subscribe to my newsletter
Read articles from Lưu Tuấn Anh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
