Booking.com Phishing Campaign Uses Unicode Character "ん" to Trick Users
 Đinh Văn Mạnh
Đinh Văn Mạnh
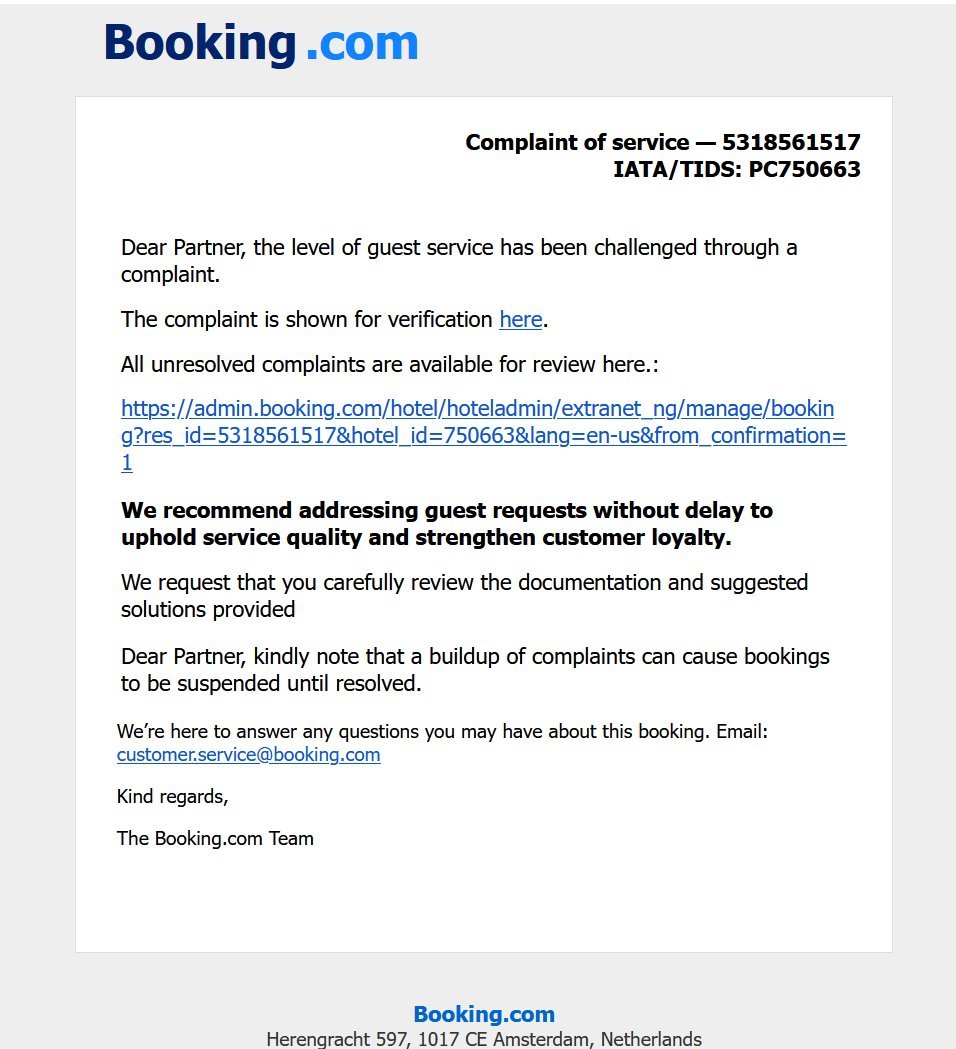
Attackers are exploiting a special Unicode character to create phishing links that look like the official Booking.com links in a new campaign to distribute malware. This attack uses the Japanese hiragana character "ん", which can appear as a slash on some systems, making the phishing URL seem legitimate to users at a glance.
Homoglyph Attack Technique
This attack, first discovered by security researcher JAMESWT, takes advantage of the Japanese hiragana character "ん" (Unicode U+3093), which resembles the Latin character sequence '/n' or '/~' in some fonts. This visual similarity allows scammers to create URLs that appear to belong to the official Booking.com domain but actually lead users to a malicious website.
This technique is a type of homoglyph attack—using characters that look similar but belong to different character sets or alphabets. For example, the Cyrillic character "О" (U+041E) can appear identical to the Latin letter "O" (U+004F) to humans, but they are different characters.

In the phishing email shared by the researcher, the text appears as "https://admin.booking.com/hotel/hoteladmin/..."** which seems like the real Booking.com address, but the actual link points to:
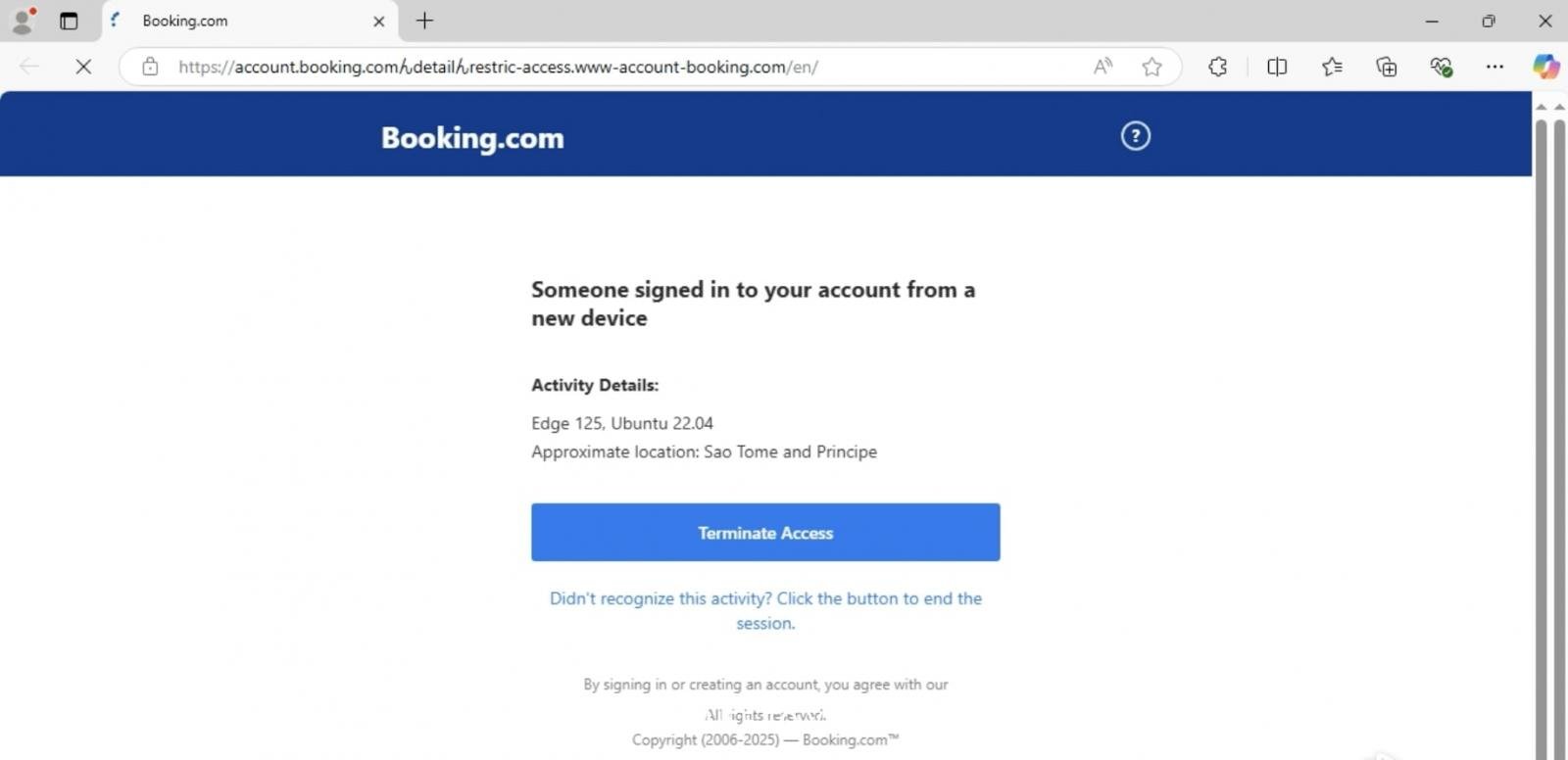
texthttps://account.booking.comんdetailんrestric-access.www-account-booking.com/en/
How Malware Works and Is Distributed
When displayed in a web browser's address bar, the characters "ん" can trick users into thinking they are navigating through a subdirectory of booking.com. In reality, the registered domain is actually www-account-booking[.]com, a fake malicious website, and everything before that is just a string of deceptive subdomains.
Victims who click the link are redirected to a malicious MSI file from a CDN link. The MSI file is used to drop further payloads, which may include an infostealer or a remote access trojan. Samples of the malicious website are available on MalwareBazaar by abuse.ch, with any.run analysis showing the infection chain.
Trends in Unicode and AI Attacks
Unicode attacks are becoming more sophisticated. According to research from Juniper Threat Labs, a new JavaScript obfuscation technique using invisible Unicode characters is being used in phishing attacks targeting branches of a US political action committee.
This technique exploits invisible Unicode characters, specifically Hangul half-width (U+FFA0) and Hangul full-width (U+3164), to hide malicious JavaScript code in white space. These attacks are highly personalized, include non-public information, and use anti-debugging measures to evade analysis.
Phishing Statistics and Economic Impact 2025
Phishing has become a leading threat with alarming numbers:
Attack Volume: An estimated 3.4 billion phishing emails are sent daily, accounting for 1.2% of global email traffic. APWG detected over 1 million unique phishing attack websites in just the first quarter of 2025.
Financial Impact: The average cost of a data breach involving phishing is about $4.88 million. In 2024, consumers reported losses exceeding $12.5 billion due to email scams, a 25% increase from the previous year.
Success Rate: Phishing is the starting point for 36% of all data breaches, making it the most reliable method for attackers to gain an initial foothold in a target network.
Impact of AI on Phishing
The advent of generative AI has revolutionized phishing. Since the launch of ChatGPT in late 2022, the volume of phishing emails has increased by 1,265%. AI enables attackers to create emails with perfect grammar, contextual awareness, and high persuasiveness that are almost indistinguishable from legitimate communications.
According to an IBM experiment, AI can build a sophisticated phishing campaign in just 5 minutes using 5 prompts, while a team of human experts takes 16 hours to complete the same task. Currently, AI-generated content is used in 82.6% of phishing emails.
Similar Intuit Phishing Campaign
BleepingComputer also discovered a separate phishing campaign targeting users with Intuit-themed emails. These emails use domains starting with "Lntuit" - something that, when written in lowercase, can resemble "intuit" in certain fonts.
The unusually narrow layout of this email suggests it is primarily designed for mobile viewing, with attackers betting that mobile users will click on the phishing link without checking carefully.
ClickFix Attack Trend
According to research from Cofense Intelligence, fake Booking.com campaigns have surged, with 47% of the total campaign volume occurring in March 2025 alone. These campaigns use the ClickFix technique, where users are tricked into performing "verification" steps that include copying and executing a script via Windows shortcuts.
Analysis shows that 75% of campaigns using fake CAPTCHA employ the fake Booking.com template, while 64% deliver RATs (Remote Access Trojans) and 47% distribute information stealers. XWorm RAT accounts for 53% of the total threat activity reports in these campaigns.
Targeted Industries
According to statistics from EasyDMARC, the most targeted industries in 2024 include:
Software and IT services: 26% of phishing attacks
Education: 8.62%
Financial services: 6.13%
The IT industry faces greater risks due to its critical role in infrastructure and access to valuable data.
Comprehensive Prevention Measures
Email and DNS Authentication
Implement email authentication protocols: Use SPF, DKIM, and DMARC to verify emails sent from your domain. DMARC allows email recipients to determine if the message is truly from the sender.
Enable DNSSEC: DNS Security Extensions help prevent DNS spoofing attacks by verifying the integrity of DNS records.
Domain Monitoring
Monitor similar domains: Proactively register common typos, alternative TLDs, and homograph variations of your organization's domain. Use domain monitoring tools or threat intelligence feeds to detect new registrations similar to your domain.
Education and Training
User awareness training: Conduct regular training sessions for employees to help them recognize phishing attempts and other spoofing tactics. Train users to identify suspicious emails, including poor grammar, urgent requests for sensitive information, or unfamiliar sender addresses.Giải Pháp Công Nghệ
Implement advanced email filtering: Use advanced email filtering solutions to detect and block phishing emails, especially those attempting to spoof domains. Anti-phishing tools leverage machine learning and real-time threat intelligence to analyze email content, sender reputation, and embedded links.
Use dedicated security tools: Specialized software and hardware like email security gateways and advanced threat protection software perform incoming message analysis to identify anomalies and block suspicious spoofed messages.
Testing and Monitoring
Conduct regular security assessments: Provide periodic evaluations of security posture through comprehensive assessments, including reviews of email system vulnerabilities, security protocol evaluations, and continuous adherence to best practices.
Continuous monitoring: Regularly monitor your domain registrations and DNS records to detect unauthorized changes. Periodic checks of these records can quickly alert you to potential security breaches before they become actual spoofing incidents.
Browser Configuration
Enable Punycode display: For Firefox users, type "about:config" in the address bar, search for "network.IDN_show_puny_code," and set the value to true to display Punycode instead of ASCII. Chrome has addressed this issue since version 58.
Use a password manager: If you are on a Unicode domain, the password manager will not be fooled and will not fill in login information in the fields. When this happens, it is a major warning sign about the site you are visiting.
Conclusion
Homoglyph attacks using Unicode characters like "ん" represent an increasingly sophisticated threat in the current phishing landscape. With the rise of AI and new obfuscation techniques, defense requires a multi-layered approach combining technology, education, and continuous monitoring.
These incidents serve as a reminder that attackers will continue to find creative ways to exploit typography for social engineering. Visually checking URLs is no longer reliable enough, requiring organizations to invest in comprehensive security solutions and raise awareness of these new threats.
References
BleepingComputer: Booking.com phishing campaign uses sneaky 'ん' character to trick you
Mesh Security: Homoglyph Email Attacks: Understanding and Mitigating the Threat
Infosecurity Magazine: Phishing Campaign Uses Fake Booking.com Emails to Deliver Malware
Cofense: ClickFix Campaign Spoofs Booking.com for Malware Delivery
Deepstrike: Phishing Statistics 2025: AI, Behavior & $4.88M Breach Costs
SentinelOne: Domain Spoofing: Definition, Impact, and Prevention
CyCognito: How Domain Spoofing Works and 8 Ways to Prevent It
TechMagic: Phishing Statistics in 2025: The Ultimate Insight
Subscribe to my newsletter
Read articles from Đinh Văn Mạnh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
