Data Integrity What It Means and Why It’s Important
 Community Contribution
Community Contribution
Data integrity refers to the accuracy, completeness, and consistency of data throughout its lifecycle. Organizations face significant risks when data accuracy is compromised, as demonstrated by recent incidents where healthcare breaches cost an average of $10.22 million in the US and pose systemic threats to patient safety. The importance of data integrity extends from data collection to migration, with vulnerabilities arising at each stage, such as unauthorized changes and synchronization issues. A data-driven organization relies on robust controls to maintain trustworthy information and prevent costly strategic failures.
| Statistic Description | Value / Detail |
| Average cost of healthcare data breach (US) | $10.22 million (2025) |
| Global all-industry average breach cost | $4.44 million |
| Number of large scale breaches (500+ records) | 725 incidents reported in 2024 |
| Average breach lifecycle in healthcare | 279 days (time to identify and contain breach) |
Maintaining data integrity safeguards decision-making and demonstrates the importance of data integrity for every organization and individual.
Key Takeaways
Data integrity means keeping data accurate, complete, and consistent throughout its entire life to ensure trust and reliability.
Maintaining data integrity protects organizations from costly breaches, supports better decisions, and builds trust with customers and regulators.
Data integrity includes physical protection of data, logical rules to keep data correct, and validation checks to catch errors early.
Strong data integrity requires clear policies, role-based access, encryption, regular backups, audit trails, and staff training.
Data integrity works hand-in-hand with data quality and data security to keep information safe, useful, and trustworthy.
Data Integrity Defined
What Is Data Integrity
Data integrity represents a foundational concept in information management. Leading authorities define data integrity as the assurance that data remains accurate, consistent, and valid throughout its lifecycle. Organizations rely on data integrity to maintain both the value and structural soundness of their information assets. This concept stands apart from data quality and data security, although it closely relates to both.
Data integrity processes protect information from unauthorized changes, corruption, and loss, ensuring that every record remains trustworthy and reliable.
A formal understanding of data integrity includes several logical dimensions:
Domain Integrity: Validates that all values in a field conform to defined rules and formats.
Entity Integrity: Prevents duplicate or null records by enforcing unique primary keys.
Referential Integrity: Requires foreign keys to correspond to valid primary keys or remain null, maintaining proper data linkage.
User-defined Integrity: Encompasses additional rules set by users to address specific business needs.
Organizations also recognize physical and logical integrity as essential components. Physical integrity protects data against hardware failures and environmental threats, using backups and disaster recovery plans. Logical integrity maintains the authenticity and consistency of data within databases and applications, applying validation rules and access controls.
| Component Type | Description |
| Physical Integrity | Ensures data is not altered or corrupted during storage and retrieval; protects against hardware failures, environmental threats, and includes backups and disaster recovery plans. |
| Logical Integrity | Maintains accuracy and consistency of data within databases and applications; includes subtypes: entity, referential, domain, and user-defined integrity. |
| Entity Integrity | Guarantees unique keys and non-null fields to prevent duplication and missing data. |
| Referential Integrity | Ensures uniform use of data across tables with rules for modification and deletion to maintain accuracy. |
| Domain Integrity | Controls valid data types and values within a domain through constraints. |
| User-defined Integrity | Custom business rules and validations tailored to specific organizational needs. |
| Core Attributes | Accuracy, Completeness, Consistency, and Validity are fundamental to data integrity, ensuring data is correct, complete, uniform, and adheres to rules. |
| Techniques to Maintain | Data validation, access controls, encryption, backups, and audit trails help preserve data integrity throughout its lifecycle. |
Contextual data integrity plays a role in adapting these principles to specific environments, such as healthcare, finance, or manufacturing. Each sector applies unique rules and standards to ensure that data remains reliable and fit for its intended purpose.
Principles of Data Integrity
International standards organizations and regulatory agencies have established foundational principles to guide data integrity. The ALCOA framework summarizes these principles:
Attributable: Data must identify who performed an action and when.
Legible: Records must be readable and permanent.
Contemporaneous: Data must be recorded at the time the work is performed.
Original: Data must be the original record or a certified true copy.
Accurate: Data must be free from errors and truthfully represent the work performed.
The ALCOA+ extension adds further requirements:
Complete
Consistent
Enduring
Available
Regulatory bodies such as the FDA and EMA emphasize these principles to ensure data reliability, traceability, and compliance throughout the product lifecycle. ISO standards, including ISO 27001 and ISO 27002, provide frameworks for information security management systems that support data integrity by enforcing confidentiality, integrity, and availability.
Organizations must implement robust systems, validation procedures, documentation, risk management, training, audits, and governance frameworks to comply with these principles and regulatory requirements.
The Data Integrity Model uses the analogy of building a house to illustrate its layered approach. The foundation consists of management leadership, a quality culture, and trained staff. The first level involves validated systems and analytical instruments. The second level focuses on correct analytical procedures. The third level is the analysis itself, which depends on the robustness of the underlying layers. This model highlights that data integrity depends on organizational, procedural, and technical foundations working together.
Regulatory requirements influence data integrity principles across sectors. Agencies such as the FDA, EMA, and MHRA impose strict guidelines to ensure product quality, patient safety, and compliance. Organizations must validate systems, manage risks, document processes, and control changes to maintain data integrity. These frameworks adapt to technological advances, such as cloud computing, ensuring ongoing compliance and data security.
Maintaining data integrity fosters trust and transparency among stakeholders. It supports reliable decision-making and enhances traceability throughout the product lifecycle. Organizations demonstrate compliance during audits and regulatory reviews by implementing governance controls, validation rules, audit trails, and access restrictions.
Types of Data Integrity
Physical Data Integrity
Physical data integrity protects information at the hardware and storage level. Organizations use data integrity mechanisms such as redundant hardware, regular maintenance, and environmental controls to prevent data loss or corruption. These measures defend against hardware failures, power outages, and environmental hazards like fire or water damage. For example, cloud backups and disaster recovery sites ensure data remains accessible even if a natural disaster destroys a primary data center.
| Measure Category | Protective Measures | Protection Against |
| Hardware Protection | Redundant hardware systems, regular maintenance, electrical surge protection | Hardware malfunctions, electrical failures |
| Environmental Controls | Temperature and humidity regulation, water and fire protection, dust control | Environmental hazards like heat, moisture, fire, dust |
| Backup Systems | Redundant power supplies, multiple data copies, regular backup testing, disaster recovery sites | Data loss from hardware failure, power outages, natural disasters |
Physical data integrity ensures structural integrity by maintaining the safety and reliability of stored data.
Logical Data Integrity
Logical data integrity focuses on the correctness and rationality of data within databases. It uses rules and constraints to maintain accuracy and consistency. Logical data integrity includes several subtypes:
Entity Integrity: Each record in a table must have a unique, non-null primary key.
Referential Integrity: Foreign keys in one table must match primary keys in another, preventing orphaned records.
Domain Integrity: Data values must fall within defined ranges or formats, enforced by data types and constraints.
User-defined Integrity: Custom business rules that address specific organizational needs.
Logical data integrity prevents anomalies such as duplicate entries, invalid data, and broken relationships. These constraints support structural integrity by ensuring data remains consistent and reliable across all operations.
Data Validation Integrity
Data validation integrity plays a critical role in maintaining overall data integrity. It ensures that data meets specific criteria before entering or moving through a system. Automated validation checks, such as sequence, limit, range, and completeness checks, help organizations detect and correct errors early. For instance, mandatory fields and format checks prevent incorrect data from entering databases, reducing operational failures.
Data validation integrity supports trustworthy decision-making by delivering accurate, consistent, and reliable data. It also enhances user access integrity by ensuring only valid and authorized data enters the system.
Continuous validation, real-time monitoring, and feedback loops further strengthen data integrity mechanisms. These practices improve operational efficiency, reduce costs, and increase user confidence in data systems. By combining physical, logical, and data validation integrity, organizations address all major types of data integrity and create robust, reliable information environments.
Importance of Data Integrity
Benefits
Organizations and individuals rely on data integrity to achieve reliable outcomes and maintain trust. High data integrity supports accurate reporting, which enables fact-based decisions in sectors such as healthcare, finance, and manufacturing. When data remains complete and consistent, companies can streamline compliance processes and improve governance.
Success metrics like reduced error rates and time saved during data processing serve as key performance indicators for data quality frameworks. By monitoring these metrics, organizations can measure the return on investment from their data integrity initiatives. Improved data quality leads to better decision-making, regulatory compliance, and operational efficiency.
A 2023 report from Drexel University’s LeBow Center of Business Analytics found that organizations with robust data governance programs experience measurable improvements. Fifty-seven percent report better analytics and insights, sixty percent observe improved data quality, and sixty-six percent identify enhanced data quality as the leading benefit. These improvements foster greater trust and confidence in data-driven decisions, which are essential for business success and customer satisfaction.
High data integrity enables organizations to identify errors quickly, maintain data health, and support real-time decisions. These advantages translate into increased productivity, reduced costs, and stronger competitive positioning.
Individuals also benefit from data integrity. Accurate personal records ensure proper healthcare treatment, secure financial transactions, and reliable educational outcomes. Data validation and protection mechanisms safeguard sensitive information, reducing the risk of identity theft and fraud.
Risks
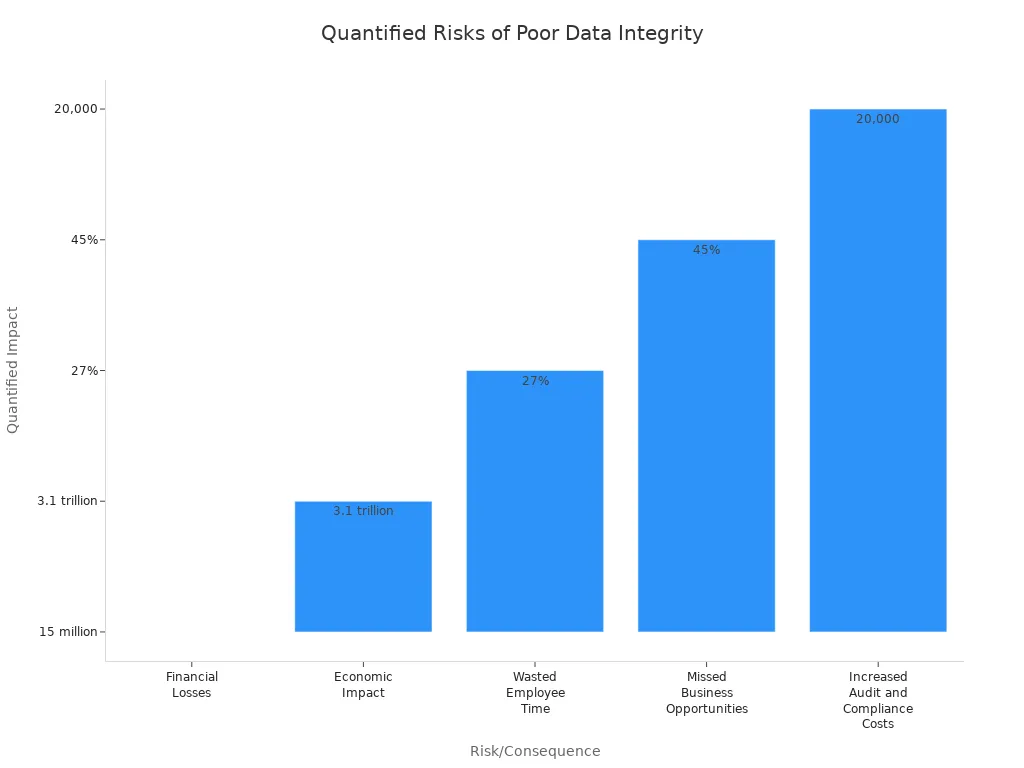
Poor data integrity exposes organizations to significant risks and consequences. Financial losses, wasted employee time, and missed business opportunities often result from inaccurate or incomplete data. The average annual loss per organization reaches $15 million, while the broader economic impact on the US economy totals $3.1 trillion.
| Risk/Consequence | Description | Quantified Impact/Example |
| Financial Losses | Lost revenue, inefficiencies, missed opportunities | Average $15 million annual loss per organization |
| Economic Impact | Broader economic burden across sectors | $3.1 trillion annual impact on US economy |
| Wasted Employee Time | Time spent validating, correcting, or searching for accurate data | Up to 27% of employee time wasted |
| Missed Business Opportunities | Loss of potential leads and market opportunities due to poor data quality | Up to 45% of potential leads missed |
| Increased Audit and Compliance Costs | Extra staff time and resources spent on audits and compliance due to poor data quality | Additional $20,000 annually per company |
| Reputational Damage | Loss of customer trust and brand damage due to inaccurate or incomplete data | Not quantified but noted as significant |
| Flawed Decision-Making | Poor strategic decisions resulting from inaccurate or incomplete data | Not quantified but highlighted as critical |
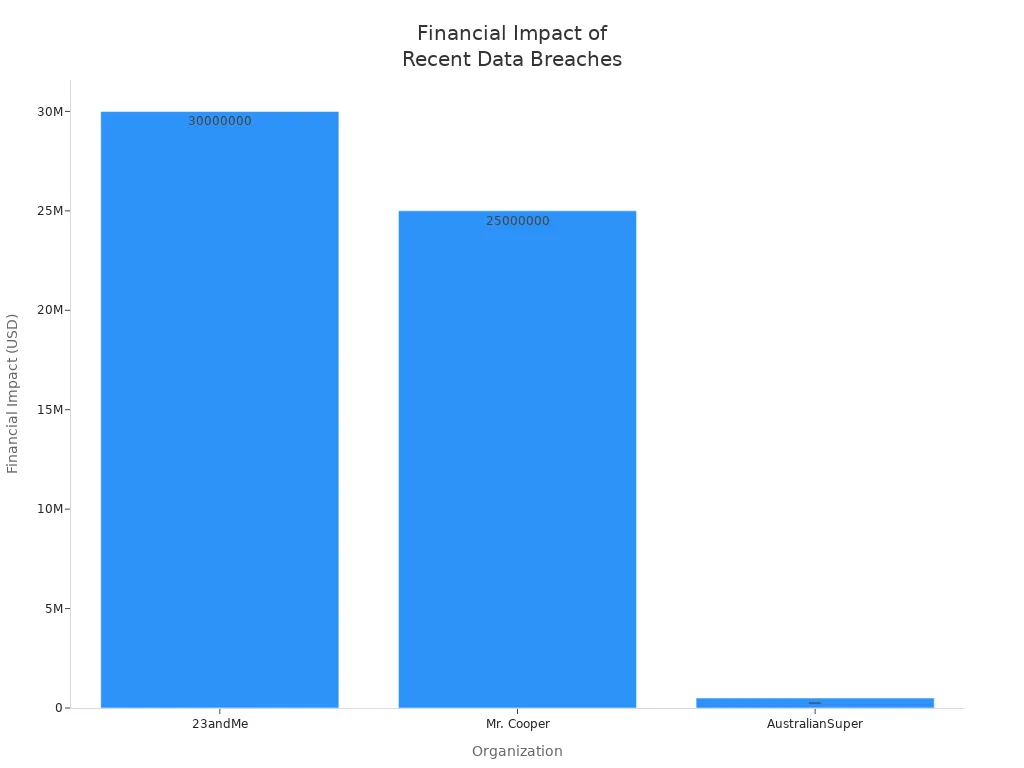
Recent case studies highlight the financial impact of data integrity breaches. The Mr. Cooper ransomware attack in October 2023 led to $25 million in response and recovery costs, including identity protection services for 14.7 million customers. The 23andMe breach exposed sensitive genetic and health data of nearly 7 million users, resulting in a $30 million settlement and a multi-year privacy monitoring program. Yale New Haven Health System provided credit monitoring services to 5.5 million affected individuals, reflecting the direct and regulatory costs of data integrity failures.
| Organization | Breach Details | Financial Impact / Response Costs |
| 23andMe | Breach affected ~7 million users; genetic and health data exposed | $30 million settlement including cash payments and monitoring program |
| Mr. Cooper | Ransomware attack affecting 14.7 million customers | $25 million spent on response, recovery, and identity protection services |
| AustralianSuper | Credential stuffing attack on thousands of accounts | $500,000 lost by 4 customers |
| WK Kellogg | Data breach involving employee and vendor data via third-party platform | Offered one year of identity theft protection services |
| Yale New Haven Health System | Breach impacted 5.5 million individuals; sensitive personal data exposed | Provided credit monitoring services to affected individuals |
Common data integrity risks include software failures, server crashes, and lack of data integration. Organizations face incompatibilities, duplications, and corrupted data sets when they use multiple analytics tools without harmonization. Insufficient data auditing allows errors to spread, reducing reliability. Outdated legacy systems increase technical debt and complicate management and security.
Software failures can damage data integrity.
Server crashes threaten data availability and consistency.
Lack of integration leads to incompatible and corrupted data sets.
Multiple analytics tools without harmonization cause unreliable insights.
Insufficient auditing allows errors to propagate.
Legacy systems increase technical debt and management challenges.
The importance of data integrity becomes clear when considering the financial, operational, and reputational risks. Effective protection strategies help organizations avoid costly breaches, regulatory penalties, and loss of stakeholder trust.
Data Integrity vs. Data Quality and Security
Data Quality
Organizations often confuse data integrity with data quality, yet each concept serves a distinct purpose. Data integrity ensures that information remains accurate, consistent, and reliable throughout its lifecycle, preventing unauthorized changes and corruption. Data quality, on the other hand, measures how well data fits its intended purpose, focusing on attributes such as completeness, relevance, and timeliness.
| Aspect | Data Integrity | Data Quality |
| Definition | Ensures data accuracy, consistency, and reliability by preventing unauthorized changes and corruption throughout the data lifecycle. | Measures how well data fits its intended purpose, focusing on accuracy, completeness, consistency, relevance, and timeliness. |
| Objective | Maintains data security and trustworthiness, protecting data from corruption or unauthorized modification. | Ensures data is accurate, relevant, and suitable for intended use, supporting decision-making and operational efficiency. |
| Key Attributes | Accuracy, consistency, reliability, security. | Accuracy, completeness, consistency, relevance, timeliness. |
| Focus | Primarily on data protection and preventing corruption or unauthorized changes. | Primarily on data fitness for use and relevance in specific contexts. |
| Mechanisms | Encryption, checksums, access controls, data validation. | Data cleansing, standardization, governance, monitoring. |
| Scope | Entire data lifecycle: creation, storage, transmission, processing. | Mainly on data usage and appropriateness within business or analytical processes. |
| Impact of Issues | Leads to data corruption, loss, unauthorized access, compromising reliability and security. | Leads to inaccurate insights, flawed decisions, inefficiencies. |
| Application | Critical in financial, healthcare, legal, and security-sensitive environments requiring strict accuracy and security. | Important for analysis, reporting, customer service, compliance, marketing, and decision-making. |
A patient's medical record that consistently displays the same blood type across all hospital systems demonstrates data integrity. In contrast, customer data with current contact details and standardized addresses exemplifies high data quality, enabling effective marketing and personalized service. Data quality initiatives, such as cleansing and validation, complement data integrity by ensuring information is accurate, complete, and fit for use. During cloud migrations, organizations use checksums and validation to prevent data loss, while data quality tools maintain consistency and usability. Together, these efforts support reliable governance and effective decision-making.
Data quality and data integrity work together to build trust in data-driven environments. Good data quality practices help detect and correct errors, directly supporting data integrity.
Data Security
Data security protects information from unauthorized access, theft, or damage. While data integrity focuses on maintaining accuracy and consistency, data security uses safeguards such as encryption, access controls, and firewalls to prevent breaches and cyberattacks.
| Key Aspect | Data Integrity / Data Protection Focus | Data Security Focus |
| Main Concern | Ensuring data accuracy, consistency, recoverability, and availability after loss or disaster | Preventing unauthorized access, breaches, and cyberattacks |
| Methods | Backup, disaster recovery, redundancy mechanisms | Encryption, access controls, firewalls, intrusion detection |
| Primary Objective | Maintain data integrity and availability; enable recovery after incidents | Protect data confidentiality and prevent unauthorized use |
| Threat Scope | Non-malicious threats like hardware failure, accidental deletion, disasters | Malicious threats including hacking, ransomware, insider threats |
| Tools | Backup solutions, disaster recovery plans, redundancy | Encryption, firewalls, multi-factor authentication, monitoring systems |
| Industry Relevance | Critical in regulated sectors (healthcare, finance) for compliance and continuity | Important across all industries, especially those handling sensitive data |
| End Goal | Restore data and business operations quickly after data loss or corruption | Prevent data breaches and maintain confidentiality |
Encryption plays a vital role in data security by converting information into unreadable formats, preventing unauthorized access. However, encryption alone does not guarantee data integrity. Organizations use additional mechanisms such as hashing and digital signatures to ensure that data remains unaltered and trustworthy. Data integrity and data security are interrelated, but each addresses different risks and requires specific controls.
Comprehensive data management demands both strong data integrity and robust data security measures to protect information and maintain trust.
Maintain Data Integrity
Threats
Organizations face a wide range of data integrity threats in modern IT environments. Human error remains the most frequent cause, with typographical mistakes, accidental deletions, and misconfigured queries leading to corrupted records. System failures, such as hardware crashes or software bugs, interrupt transactions and create partial or lost data. Cybersecurity threats, including ransomware and insider manipulation, can encrypt, modify, or fraudulently alter sensitive information. Supply chain attacks introduce compromised code into trusted systems, as seen in incidents like the 3CX breach and Codecov pipeline attack. Poor data integration practices during migration or consolidation often result in mismatched fields, duplication, or data loss. These challenges require a data integrity manager to monitor and address vulnerabilities, ensuring user access integrity and ongoing protection.
Human error: accidental deletion, misconfiguration, inconsistent formatting
System failures: hardware/software crashes, interrupted transactions
Cybersecurity: ransomware, insider fraud, supply chain attacks
Poor integration: migration errors, duplication, field mismatches
Software integrity failures: compromised packages, untrusted updates
Best Practices
Industry leaders recommend a comprehensive data integrity solution to address these risks. Organizations should implement data validation and verification checks at every entry point. Role-based access controls restrict modifications to authorized personnel, while encryption protects sensitive data in transit and at rest. Regular backups and recovery plans enable restoration after loss or corruption. Data versioning and timestamps help track changes and support rollback. Audit trails and logs provide transparency for monitoring and forensic analysis. Error handling mechanisms detect and resolve inconsistencies quickly. Data quality checks identify and correct duplicates or outdated records. A robust data integrity manager oversees governance policies and employee training, fostering a culture of compliance and vigilance. Automated data discovery tools and observability platforms enhance real-time monitoring and validation.
Validate and verify data at entry
Restrict access with role-based controls
Encrypt data for security and protection
Back up data regularly and maintain recovery plans
Track changes with versioning and timestamps
Maintain audit trails and logs
Detect errors with automated alerts
Conduct regular data quality checks
Establish governance policies and train staff
Industry Examples
Data integrity applications span multiple industries, each facing unique challenges. In pharmaceutical manufacturing, poor records management and falsified data have led to FDA warning letters, fines, and reputational damage. Marketing teams struggle with inaccurate customer insights and unreliable analytics, reducing ROI and sales support. IT operations encounter inconsistent access, data loss, and unreliable reporting, often due to legacy systems and poor integration. Compliance failures in healthcare and finance result in regulatory penalties and even physical harm. A data integrity manager and data integrity analyst play critical roles in developing a data integrity strategy and implementing effective data integrity measures. Successful organizations use regular backups, error checking, immutable storage, and employee training to ensure data integrity and prevent costly data integrity issues.
A strong data integrity solution, supported by dedicated management and continuous monitoring, helps organizations maintain trusted data, avoid operational disruptions, and meet regulatory requirements.
Data integrity plays a vital role in business and daily operations. Organizations benefit from regular audits, strong governance, and secure data handling.
Protect information with encryption and access controls.
Verify accuracy after transfers and monitor for discrepancies.
Train teams and update policies to adapt to new challenges.
Continuous improvement depends on vigilance, clear standards, and a culture of accountability. Every organization should assess current practices and address gaps to strengthen data reliability.
FAQ
What is the difference between data integrity and data security?
Data integrity ensures information remains accurate and consistent. Data security protects information from unauthorized access or attacks. Both work together to keep data trustworthy and safe.
How can organizations detect data integrity issues?
Organizations use automated validation checks, audit trails, and regular data quality reviews. These tools help identify errors, unauthorized changes, or inconsistencies quickly.
Why does data integrity matter in healthcare?
Data integrity in healthcare protects patient safety. Accurate records support correct diagnoses, treatments, and billing. Errors can lead to harmful outcomes or legal issues.
Subscribe to my newsletter
Read articles from Community Contribution directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
