150+ Mozilla Extensions, One Backend, and the Paid Media Problem
 Phish Destroy
Phish Destroy
Recently, a story about “150+ fake Mozilla extensions” tied to a supposed “Russian trail” has been amplified across major crypto and security outlets. It sounds dramatic, but our analysis shows this narrative is misleading — and worse, it shields the real perpetrators.
Press enter or click to view image in full size
generated image
We are publishing this as a volunteer threat intelligence group. We don’t charge for our work, we don’t monetize, and we don’t chase clout. We follow the threats, collect evidence, and speak when false narratives undermine real investigations.
150+ Low-Quality Extensions on a Single Backend
All extensions in this campaign were:
- non-unique, copy-paste quality;
- only logos and names varied;
- and all connected to a single backend.
Backend IP: 185.208.156.66
Press enter or click to view image in full size

we see this backend where site POST seed from extension alladdsite[.]digital/app.php
185.208.156.66 - urlscan.io
urlscan.io - Website scanner for suspicious and malicious URLs
Example: https://urlscan.io/result/0198e619-7b76-74a0-b581-c2e788879572/
Checking all domains tied to this IP today, most are dead. But at the time, we archived everything. Urlscan and WebArchive preserve snapshots of sites we reported.
Our Actions Against This Campaign
As a volunteer threat intelligence group, we specialize in takedowns of phishing and scam infrastructure. In this case, we:
Submitted reports directly to Mozilla to flag malicious extensions.
Escalated links and evidence to Seal, requesting professional assistance to accelerate the banning process.
Published a report on Chainabuse, ensuring the wider community could see and validate the threat.
Injected millions of empty seed phrases into the attackers’ backend, intentionally polluting their data so they wasted time processing fake entries instead of stealing from victims.
Takedown operations are our core contribution: identifying, reporting, and helping to dismantle malicious infrastructure as quickly and effectively as possible.
Why This Is Not “Russian” Infrastructure
We’ve analyzed Russian-speaking threat actors for years. Their tactics look very different:
- Distributed backends (Cloudflare Workers, Firebase, Amazon, unique links per campaign).
- Obfuscation and redundancy to avoid single points of failure.
- They do not route all data into one static backend.
But here, we see:
- A Nigerian hosting provider.
- Neighboring domains tied to bank scams, fake crypto wallets, fake delivery scams.
- A Telegram account receiving stolen data — linked to a Nigerian operator.
Screenshot: https://imgur.com/kAC571J
Russian groups build sophisticated infrastructures. This was cheap, centralized, and unsophisticated — exactly what we’ve seen before on Nigerian servers.
Related Work
We previously analyzed IPs on the same hosting provider:
https://phishdestroy.io/registrars-enabling-global-scams
And created an archive of processed domains:
https://phishdestroy.github.io/Nigerian-dignity/out/index.html
The Paid Media Problem
This is where the real danger begins.
We know that paid media placements are common practice. But the consequences in cybersecurity are serious:
- One paid article in a “respected” outlet gets published.
- Hundreds of smaller sites, blogs, and Telegram channels rewrite or translate it.
3. Within days, it becomes a massive fake narrative with the illusion of credibility.
Victims see “the Russian trail,” believe the case is closed, and stop reporting to authorities. Real criminals remain untouched.
Example: Angel Drainer
Press enter or click to view image in full size

Similar news stories appeared in all major media outlets.

Well, Angel himself wrote the reply, and it still works. AngelFerno
Every outlet ran headlines about “Angel Drainer shutdown after devs identified.”
But was it true — or just another paid placement, repeated everywhere until it looked credible?
For criminals, buying a few articles is pocket change. For victims, it changes everything: investigations stall, truth gets buried.
**Cybersecurity Companies Buying Their Own PR
Here is another uncomfortable truth.**
We see cybersecurity companies paying tens of thousands of dollars for articles about themselves, their “research,” their “impact.”
This raises fundamental questions:
- Why does a real cybersecurity group need to pay for coverage?
- Are they trying to bury the real hacker’s trail?
- Or worse, to leverage the hacker’s identity for blackmail or competitive gain?
- Is the purpose to strengthen trust — or to manipulate perception for profit?
If cybersecurity becomes another PR game, where facts are shaped by who pays more, then trust in this field collapses. Instead of protecting victims, it risks protecting criminals.
Evidence of the Market
The practice is not hidden.
- On Fiverr, Upwork, and specialized PR markets, you can directly purchase “guest posts.”
- Ask providers, and they send Google Sheets with dozens of outlets and prices — including well-known cybersecurity brands.
- Some even promise: “for an extra fee, no sponsored label.”
Example:
Press enter or click to view image in full size

Screenshot example of paid publication listings. Platforms like this offer placement in major crypto media for thousands of dollars. And there are many such services — this is only one sample among dozens available online.
We also registered on PR platforms to see the goals listed for buying media
coverage:
Press enter or click to view image in full size

Example form from a media-publishing platform. Among the stated goals for buying articles: SEO, sales traffic, brand awareness, reputation management, social verification, and even publication lists for visa applications.
Press enter or click to view image in full size
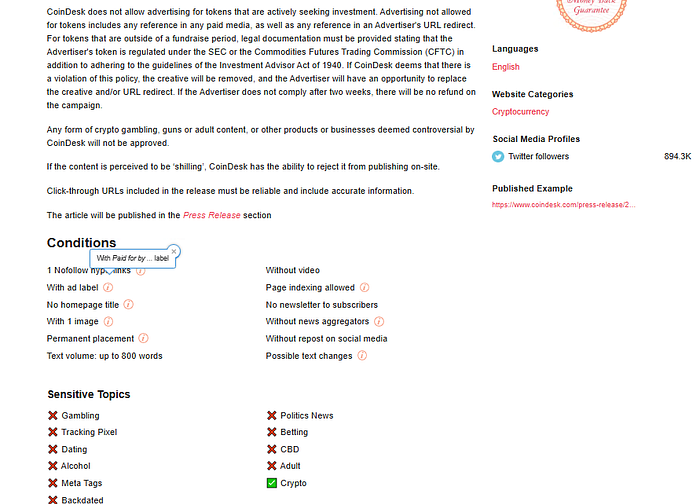
Example of conditions for a paid publication slot. Note the restrictions (ad label, no homepage placement, no social reposts) and the list of sensitive topics.
Press enter or click to view image in full size

Example of a paid “interview” slot offered by a major crypto media outlet, priced over $20,000. Some buyers clearly invest in such expensive placements. On outsourcing markets, however, offers exist with lower prices and sometimes without an “ad” label — though transparency is not guaranteed.
The stated goals include:
- Link Building (SEO)
- Traffic & Sales
- Brand Awareness
- Reputation Management (burying negatives)
- Social Verification
- Publication Lists for Visa Applications
This is not journalism. It is a market — where credibility is bought and sold.
Business vs. Lies
Publishing paid content is not illegal. It’s business.
But when paid content crosses into:
- publishing false claims,
- misdirecting investigations,
- disguising PR as fact,
…it becomes part of the problem, not the solution.
Conclusion
We are a volunteer cybersecurity initiative.
- We don’t get paid.
- We don’t sell ads.
- We don’t profit.
Our mission is to identify threats and protect victims.
The facts are clear:
- 150+ Mozilla extensions routed to a single backend on Nigerian hosting.
- Data went to a Nigerian Telegram account.
- The “Russian trail” narrative is fabricated.
- Paid media coverage amplified this fabrication until it looked like truth.
- Even cybersecurity companies themselves pay huge sums for self-promotion, raising serious questions about motives.
This is the uncomfortable truth:
Selling ads is business.
Selling lies as facts shields criminals.
And when even cybersecurity sells narratives, the victims — and justice — lose.
Disclaimer
We are not accusing any individual, company, or media outlet. All facts referenced here are open-source and verifiable through public archives, scanners, and reports.
The real question is: why are such narratives controlled and amplified? Who benefits when an unknown “security company” suddenly publishes a “mega-investigation” that is inaccurate, expensive to stage, and shifts attention away from the real actors?
Is the purpose reputation management? Funding? Or even something as pragmatic as building a “publication list” to support immigration or visa applications?
These are uncomfortable questions, but they must be asked if we want cybersecurity to remain grounded in truth rather than narratives.
Subscribe to my newsletter
Read articles from Phish Destroy directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Phish Destroy
Phish Destroy
Full-stack developer with 7 years of experience building scalable web applications. Passionate about creating intuitive user interfaces and robust backend systems. I love solving complex problems and turning ideas into working code. Constantly learning new technologies to improve performance and security.