How to keep GitHub Actions up-to-date with Dependabot
 Maik Hummel
Maik Hummel
GitHub Actions are essential in today's CI/CD automation and are crucial in accelerating engineering teams. Leveraging the existing ecosystem of ready-built actions from the marketplace reduces the effort in configuring many use cases.
Building and pushing docker images with GitHub Actions is as easy as referencing them through: uses: docker/build-push-action@v2 While it is not mandatory to fix the action's version (@v2 in this case), it is a good practice to prevent breaking changes from affecting existing pipelines. However, the versioning of dependencies results in maintenance requirements.
Once the pipelines ran, I caught myself not paying attention to regularly keeping the versions up-to-date – especially if the job configurations are spread across several repositories or even GitHub organizations. This can lead to unwanted side effects over time:
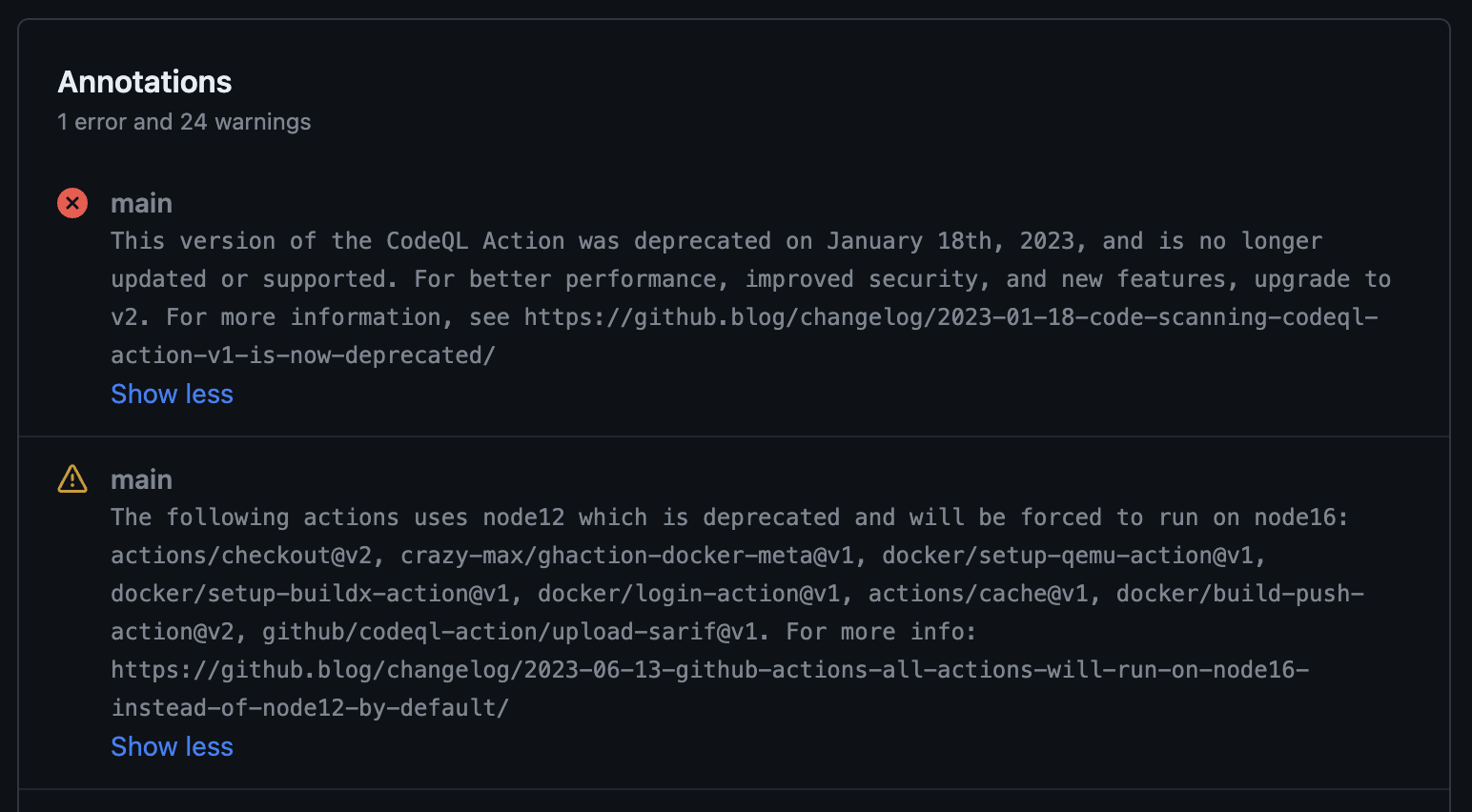
Fortunately, Dependabot has our back and supports updating GitHub Actions with automated pull requests. Depending on your organization's settings, this might not be enabled by default, and you might want to explicitly configure the update policy for GitHub Actions. To keep all my GitHub Actions updated, I added the following configuration to the .github/dependabot.yml file of my repositories:
version: 2
updates:
- package-ecosystem: "github-actions"
directory: "/"
schedule:
interval: "weekly"
day: "wednesday"
time: "13:37"
timezone: "Europe/Berlin"
open-pull-requests-limit: 1
The configuration enables weekly updates on Wednesdays at 13:37 Berlin time. To prevent Dependabot from spamming the repository with too many concurrent PRs, we are limiting this routine to a single pull request. Dependabot will subsequently automatically open PRs for all new GitHub Action releases. The PR pipelines are most often a good indicator for breaking configuration changes, but it might be worth checking the individual release notes.
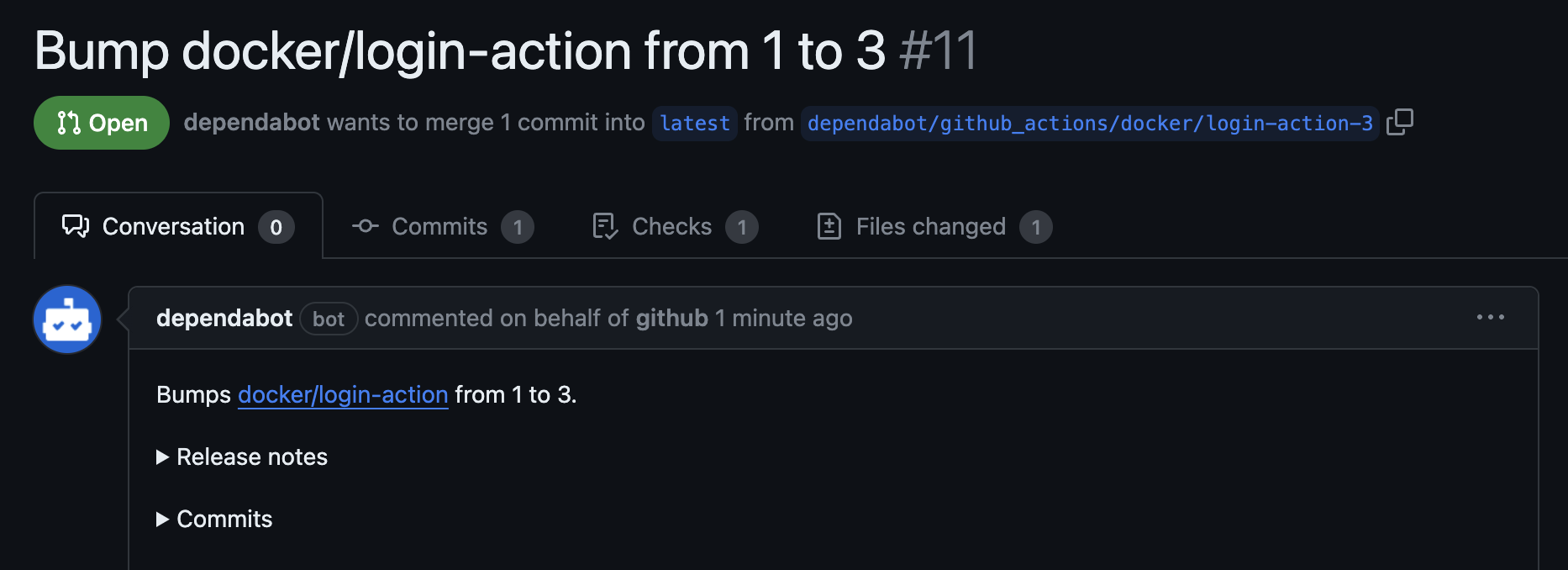
This should keep all maintained GitHub Actions updated, but be aware that they are sometimes discontinued, renamed, or forked. So, it's worth checking the referenced Actions from time to time.
Hint: Failed jobs with Dependabot
Depending on your pipeline configuration, you might experience failing jobs. This can be caused by missing Dependabot secrets. For security reasons, Dependabot cannot access the default secrets configured for the repository. You can specify Dependabot secrets in the repository's settings at Settings > Security > Secrets and variables > Dependabot.
Further references
Subscribe to my newsletter
Read articles from Maik Hummel directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
